AI
|Jan 17, 2026
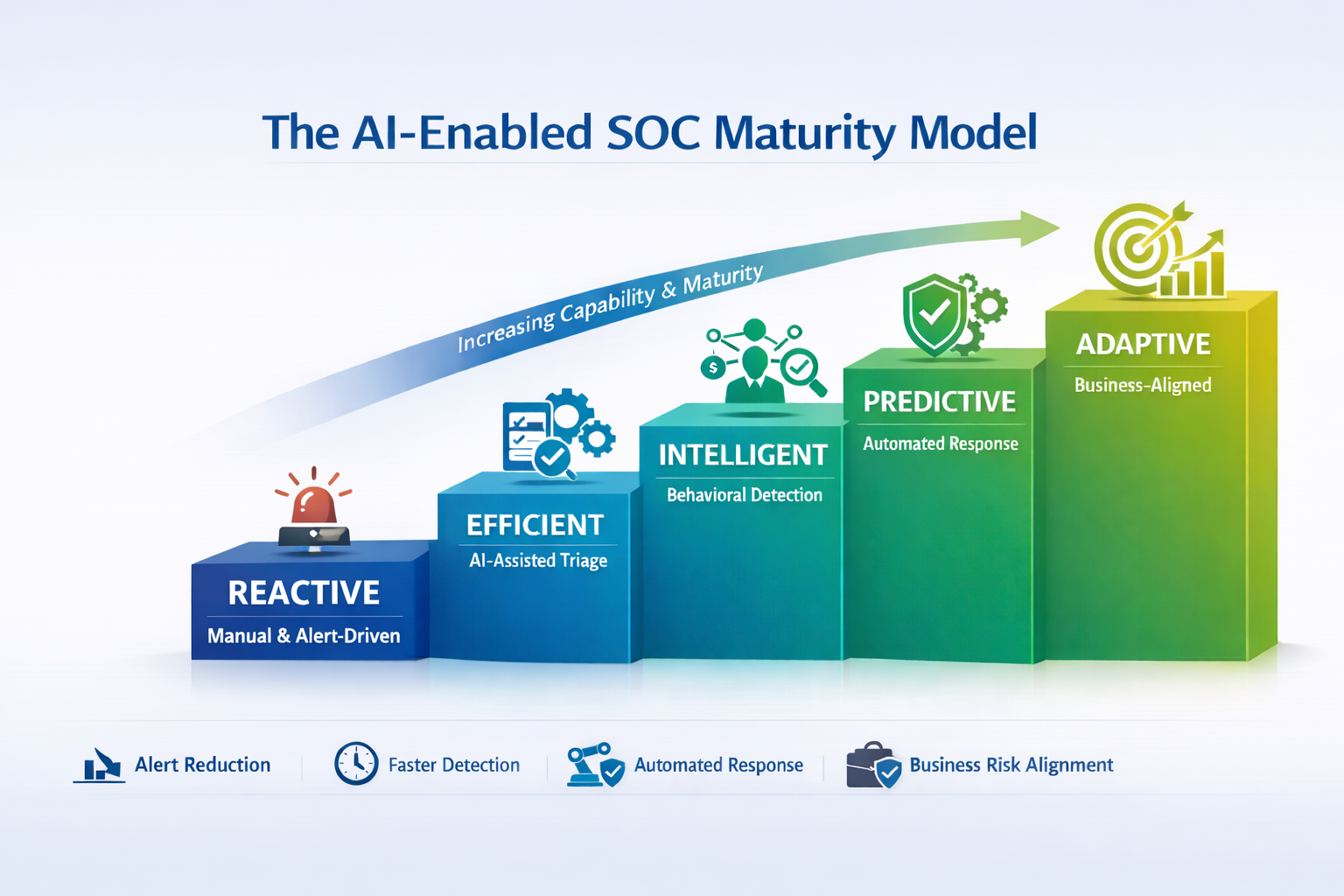
The AI-Enabled SOC Maturity Model
Security Operations Centers do not mature overnight. Most evolve through distinct stages, shaped by
Read BlogInsights for a safer digital world.
AI
|Jan 17, 2026
Security Operations Centers do not mature overnight. Most evolve through distinct stages, shaped by
Read Blog
vCISO
|Dec 20, 2025
vCISOs provide immense value by helping organizations align their security strategy with their busin
Read Blog
Incident Response
|Nov 16, 2025
Wiper malware has evolved from a niche state-sponsored tool to a mainstream destructive capabil
Read Blog
Security Awareness Training
|Oct 05, 2025
Every October, organizations and individuals around the world observe Cybersecurity Awareness Month
Read Blog
Incident Response
|Sep 14, 2025
In cybersecurity, the ability to respond swiftly to an attack is critical — but before you can res
Read Blog
Social Engineering
|Aug 16, 2025
In today’s threat landscape, protecting employees from help desk scams is not just an IT concern�
Read Blog
vCISO
|Jul 20, 2025
Running cybersecurity without a Chief Information Security Officer (CISO) is possible, especially in
Read Blog
Trends
|Jun 15, 2025
As we hit the midpoint of 2025, the cybersecurity landscape continues to shift rapidly, with threat
Read Blog
Architecture
|May 17, 2025
In an era where data breaches and cyberattacks are growing in frequency and sophistication, traditio
Read Blog
Incident Response
|Apr 19, 2025
In an era where data is one of the most valuable assets, data breaches have become increasingly comm
Read Blog
Digital Forensics
|Mar 16, 2025
IntroductionIn an era where digital threats are evolving rapidly, digital forensics has become an es
Read Blog
Incident Response
|Feb 15, 2025
Incident response is a critical aspect of cybersecurity and risk management, structured around three
Read Blog
Security Assessment
|Jan 18, 2025
Cybersecurity Risk Assessment: Why It Matters In today’s digital landscape, cyber threats are bec
Read Blog
Security Assessment
|Dec 15, 2024
A Cybersecurity Threat Assessment is a process used to identify, evaluate, and prioritize potential
Read Blog
Security Assessment
|Nov 10, 2024
A security assessment involves evaluating an organization's security posture to identify vulnerabili
Read Blog
Incident Response
|Oct 19, 2024
The Post-Incident Activity phase is often the most overlooked yet crucial part of the Incident Respo
Read Blog
Security Awareness Training
|Sep 15, 2024
Yes, phishing tests matter — a lot. They help organizations assess their employees' ability to rec
Read Blog
Incident Response
|Aug 17, 2024
Absolutely! Preparation is the foundation of an effective Incident Response (IR) Plan and is often c
Read Blog
Security Assessment
|Jul 13, 2024
In today’s digital landscape, cyber threats are becoming more sophisticated, making it imperative
Read Blog
Incident Response
|Jun 15, 2024
In today’s digital landscape, cyber threats are an ever-present danger for businesses, organizatio
Read Blog
Threat Monitoring
|May 12, 2024
In today’s fast-paced digital landscape, cyber threats are evolving at an unprecedented rate. Orga
Read Blog
vCISO
|Apr 13, 2024
In today’s digital landscape, cybersecurity threats are evolving at an alarming rate. From data br
Read Blog
Security Awareness Training
|Mar 09, 2024
In today’s digital age, cyber threats are more sophisticated and prevalent than ever. Hackers are
Read Blog
Threat Intelligence
|Feb 04, 2024
In today’s rapidly evolving digital landscape, organizations face a growing number of cyber threat
Read Blog
Insider Threat
|Jan 13, 2024
In today’s cybersecurity landscape, organizations often focus on defending against external t
Read Blog
Threat Intelligence
|Dec 10, 2023
In the ever-evolving landscape of cybersecurity threats, one group has gained notoriety for its high
Read Blog
Digital Forensics
|Nov 04, 2023
IntroductionIn an age where cyber threats are more prevalent than ever, digital forensics has become
Read Blog